How to implement Terraform automation within GitHub Actions for your B2B SaaS tool
We all start using terraform as a CLI tool on our local machine to bootstrap our initial infrastructure. We of course manage the tf state somewhere in a bucket within our cloud account. This works great as a small team with limited infrastructure needs. But as our company grows and we have more than 1 person modifying infrastructure, it becomes a hard requirement to use terraform collaboratively within a shared pipeline.
In this tutorial we will share how you can create a GitHub action that performs an apply to your environment every time you merge a PR to your main branch it will perform an infrastructure apply within your environment. You can find an example of this pipeline here

To implement Terraform collaboration within GitHub Actions, you can set up a workflow that automates the process of provisioning and managing infrastructure as code (IaC). Here's a high-level overview of how you can do this:
Step 1: Repository Setup
Ensure that your Terraform configurations and code are stored in a GitHub repository.
Step 2: Secrets ManagementStore sensitive data and credentials securely as GitHub secrets. These secrets can be accessed within your GitHub Actions workflow.
Step 3: Create a GitHub Actions WorkflowCreate a .github/workflows directory in your repository if it doesn't already exist.
Create a YAML file (e.g., terraform.yml) within this directory to define your GitHub Actions workflow.
Here's a sample terraform.yml workflow for Terraform collaboration:
name: Terraform Workflow
on:
push:
branches:
- main
jobs:
terraform:
runs-on: ubuntu-latest
steps:
- name: Checkout code
uses: actions/checkout@v2
- name: Set up Terraform
uses: hashicorp/setup-terraform@v1
with:
terraform_version: 1.5.7
- name: Initialize Terraform
run: terraform init
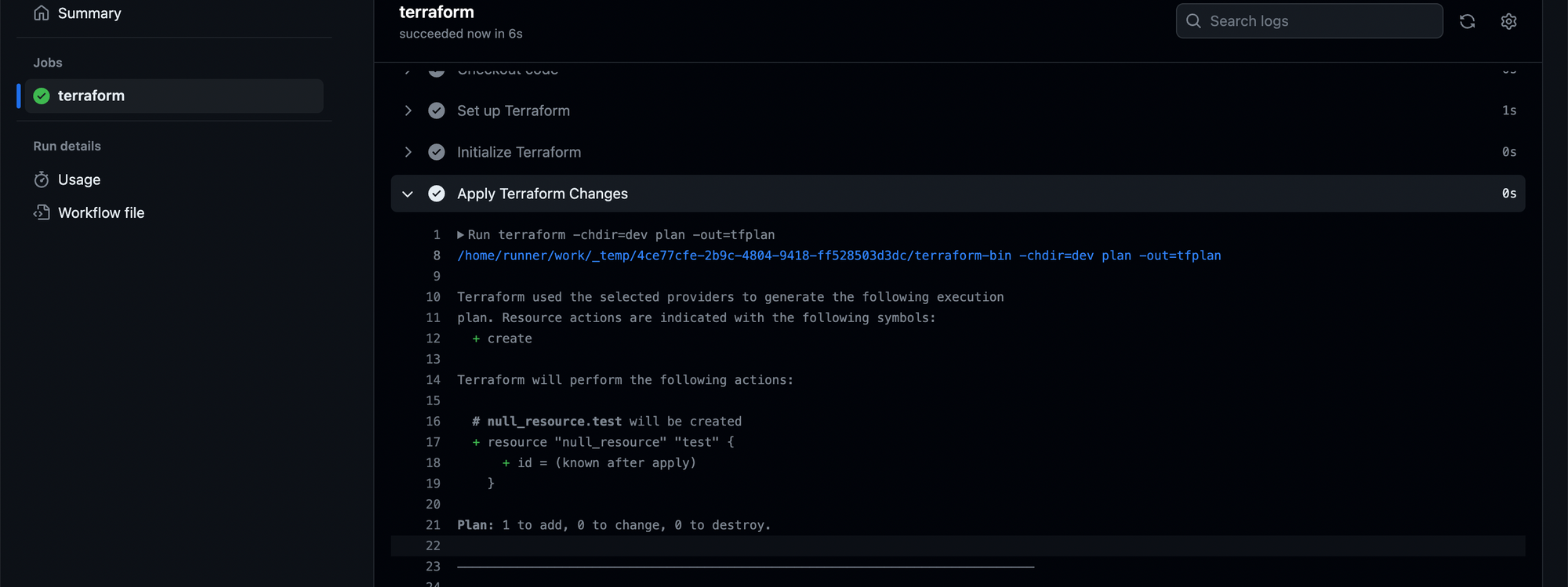
- name: Apply Terraform Changes
run: |
terraform plan -out=tfplan
terraform apply -auto-approve tfplan
env:
TF_VAR_1: ${{ secrets.TF_VAR_1 }} # Set environment variables for your secrets
Step 4: Workflow Explanation
- This workflow triggers on pushes to the
mainbranch (you can adjust the branch as needed). - It checks out your repository's code.
- It sets up Terraform using the
hashicorp/setup-terraformaction. - It initializes Terraform, plans, and applies changes.
- Sensitive data and credentials are passed as environment variables (TF_VAR_1, TF_VAR_2) to Terraform.
- Optionally, you can add a step to destroy infrastructure.
Step 5: Secrets Configuration
Make sure to add your sensitive data (e.g., AWS access keys) as secrets in your GitHub repository. These secrets are securely passed to your workflow as environment variables.
Step 6: Workflow Customisation
Customize the workflow to match your specific Terraform configuration files, variables, and providers.
Step 7: Workflow Automation
Once your workflow is configured, it will automatically run whenever changes are pushed to the specified branch. You can view workflow runs, logs, and results in the GitHub Actions tab of your repository.
By following these steps, you can effectively implement Terraform collaboration within GitHub Actions, enabling automated infrastructure provisioning and management for your B2B SaaS project.
While setting up a collaborative Terraform configuration within GitHub Actions is relatively straightforward, certain aspects can be challenging for many teams. This is where Digger comes into play. Digger is an IaC automation tool that simplifies and streamlines the process, addressing some common challenges:
Enterprise Support: For organizations with enterprise-level needs, obtaining the necessary support can be a complex requirement. Digger.dev provides the support needed to meet enterprise demands. (Audit trails, SSO, Policies as Code for compliance, etc.)
Effortless Configuration: Achieving a similar collaborative setup as described earlier, quickly and reliably, often requires expertise that not all teams possess. Digger offers a solution that minimises the effort required for configuration, making it accessible to a broader range of users.
Predictable Usage Contract: Ensuring that your infrastructure can be readily depended upon by other systems is crucial. Digger provides a predictable usage contract, promoting stability and compatibility.
Role-Based Access Control (RBAC): Managing RBAC can be challenging, but Digger simplifies this aspect, allowing you to define and enforce role-based access control efficiently.
Incorporating Digger into your IaC workflow can help you overcome these challenges and streamline your infrastructure management process, making collaboration even more efficient and hassle-free.
