Top self-hosted runner solutions for GitHub Actions.

While talking to users using Digger in GitHub Actions, we see a lot of compliance heavy enterprises relying on Self Hosted runners. We decided to compile a list of available solutions out there, to help present the options available before a decision is made. Let's dive in:
Actions runner controller
The actions/actions-runner-controller is a Kubernetes-based solution for self-hosting GitHub Actions runners. It supports GitHub Enterprise Server and allows registration at various scopes including enterprise, organization, repository, labels, and runner groups. Featuring dynamic scaling based on workload, it supports multiple architectures like x86, AMD64, ARM, and ARM64, and includes auto-deregistration and clean-up capabilities. It also offers an IssueOps project for self-service setup, supports auto-scaling to optimize resource utilization, and aims to minimize idle costs through efficient management of runner pods.
Philips Labs Terraform AWS GitHub Runner
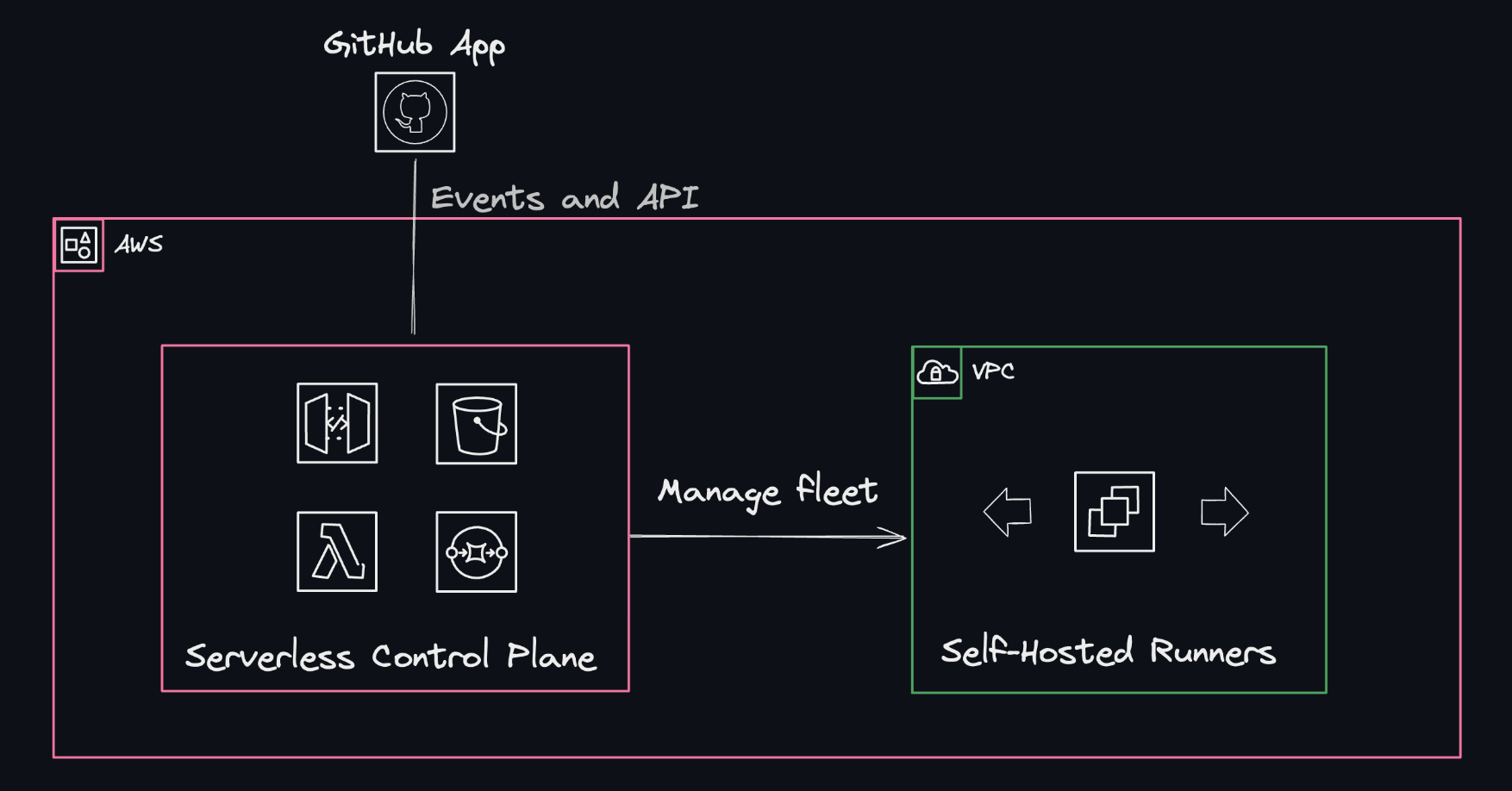
The philips-labs/terraform-aws-github-runner Terraform module streamlines the deployment of self-hosted, auto-scaling GitHub Actions runners on AWS, leveraging spot instances for cost efficiency. It employs AWS Lambda for dynamic scaling, activating additional runners based on workload demands and scaling back to zero during idle periods to eliminate unnecessary expenses. This module emphasizes security by using ephemeral runners that terminate post-task, ensuring a clean slate for each job. It supports both Linux and Windows runners, caters to various hardware and software configurations through custom AMIs, and accommodates a range of instance types and network settings. Users can create multiple runner setups from a single deployment, suitable for GitHub Cloud and GitHub Enterprise Server, focusing on organizational and repository-level runners. To get started, one needs to set up an AWS account, create a GitHub App, prepare the necessary lambdas, and deploy via Terraform. The module's documentation offers comprehensive guidance, including example configurations for different use cases, facilitating an easy setup process for users.
Docker-github-actions-runner
The myoung34/docker-github-actions-runner project offers a solution for running self-hosted GitHub Actions runners with Docker-in-Docker capabilities. This setup is designed to provide a more controlled and secure environment for CI/CD workflows, with the flexibility to handle various tasks through Docker. The project acknowledges security considerations, especially concerning environment variables, and provides detailed guidance on setup and usage. It supports a range of Docker artifacts and offers extensive configuration options through environment variables to tailor the runner's behavior and integration with GitHub.
Ansible-github_actions_runner
The MonolithProjects/ansible-github_actions_runner Ansible Role automates the deployment and management of GitHub Actions self-hosted runners on Linux and macOS. It supports various deployment scopes, including enterprise, organization, and repository levels, offering flexibility for diverse GitHub environments. The role caters to multiple CPU architectures, ensuring compatibility across a wide range of systems. Its thorough documentation guides users through installation, redeployment, and runner management processes, providing a robust solution for integrating GitHub Actions runners into their CI/CD pipelines. For a deeper dive, the GitHub repository offers comprehensive resources.
Openshift-actions-runner-installer
The redhat-actions/openshift-actions-runner-installer is a GitHub Action designed for deploying self-hosted GitHub Actions runners on Kubernetes, including OpenShift clusters. It simplifies the process by automating the detection and creation of runner containers, leveraging the OpenShift Actions Runner Chart for installation. This action ensures that necessary runners are available for workflows by checking for existing runners with specified labels and skipping the installation if such runners are already present. It is compatible with any Kubernetes platform, not just OpenShift, broadening its applicability. For more detailed information, you can visit the GitHub repository.
Reference: The source for this article is this github repository by jonico, feel free to check it out and contribute!
Digger - An Open Source orchestrator for Terraform
Thank you for reading until the end. Before you go, I just wanted to share the following:
- We’re building an Open Source Tool that helps you orchestrate Terraform and OpenTofu within CI/CD systems such as GitHub Actions while providing RBAC via OPA, Drift Detection and Concurrency with a self hostable orchestrator backend. Would love your feedback!
- Star us on GitHub | Check out Docs | Blog | Slack
